OpenSSL 3.4.0 introduced the jitter‑based entropy source (JITTER) as an optional RNG seed, accessible when compiled with enable‑jitter. In OpenSSL 3.5.0 – the new long‑term stable (LTS) release – the jitter entropy provider remains available and gains further significance: notably, the FIPS provider can optionally utilize it via a new configuration flag, enable‑fips‑jitter. This makes OpenSSL 3.5.0 particularly compelling for users seeking stablity and flexibility across both standard and FIPS and Common Criteria use cases.
NDcPP v4.0 vs. v3.0e: What’s Changing and How to Prepare
If you ship network devices into environments that care about Common Criteria, the Network Device Collaborative Protection Profile (NDcPP) is the baseline you live with. NDcPP v3.0e has been the approved version since December 2023; the ND iTC is now iterating on a NDcPP v4.0 draft. This post offers a practitioner’s comparison of v3.0e and the v4.0 draft, the NIAP acceptance window you need to plan around, and concrete steps to de‑risk your roadmap.
[Update Feb 2026: NDcPP v4.0 has now been published.]
Read MoreAccelerate Your EU Common Criteria Certification with Lightship Security & Applus+ Laboratories
At Lightship Security, we help leading security product vendors achieve NIAP and EUCC Common Criteria certification quickly and efficiently. As part of Applus+ Labororatories, a global leader in testing, inspection, and certification, we offer a powerful combination of deep technical expertise, automated evaluation tools, and global certification reach.
Why Lightship and Applus+?
Read MoreKey Update in NIAP Policy Letter #12: Vendors, Take Note of Core Functionality Requirement
The latest update to NIAP Policy Letter #12 (Update 5) brings a significant change that vendors should be aware of: the inclusion of core functionality as a critical requirement for products undergoing evaluation under NIAP. This new addition places an important responsibility on vendors to ensure that their products’ core functionality is explicitly included in the scope of evaluation. Let’s dive into why this change is so crucial for vendors and how they can prepare.
Read MorePost-Quantum Crypto – FIPS Standards Announced
[Update Sept 2024: These Standards have been published.]
In our last article on Post Quantum Crypto (PQC) titled “Introduction to the Quantum Computing Impact on Cryptography”, we introduced quantum computing concepts and the potential impact on computer security and cryptography. The article also introduced CNSA 1.0 and CNSA 2.0 as initial suites of PQC algorithms developed by the National Security Agency (NSA). The thrust of PQC development has focused on the replacement of public key cryptography given quantum computing’s ability to conduct complex calculations quickly and potentially decrypt data encrypted with legacy algorithms in hours or days, versus the years it would have normally taken.
Read MoreESV for Common Criteria
NIAP recently released Labgram #118 – Entropy Source Validation Certificates. It mandates that ESV certificates must be included as part of the Entropy Assessment Report (EAR) for all products that enter evaluation with NIAP from January 1st, 2025. Effective immediately, vendors may submit EARs that refer to an ESV certificate. This blog post discusses what ESV is, how it relates to Common Criteria under NIAP and the impact of this policy on vendors undertaking evaluations outside of NIAP (e.g. Canada etc.) but seeking NIAP PCL entry.
Read MoreEUCC Perspectives
In this post we examine the proposed European Cybersecurity Certification Scheme (EUCC). We’ll cover:
- What is EUCC?
- What is the status of EUCC?
- What has changed since the draft EUCC regulation was published?
- What impact will EUCC have on vendors?
- What impact will EUCC have on the certification industry?
- How is Lightship Security preparing for EUCC to support our clients?
What’s the Deal With NDcPP 3.0?
NDcPP 3.0E has now been endorsed by NIAP. This post aims to answer the most common questions we get about NDcPP 3.0E:
- What’s new in NDcPP 3.0E?
- What will the transition period be between NDcPP 2.2E and NDcPP 3.0E?
- What does this mean for current NDcPP projects?
- What does Lightship Security recommend for new network device projects?
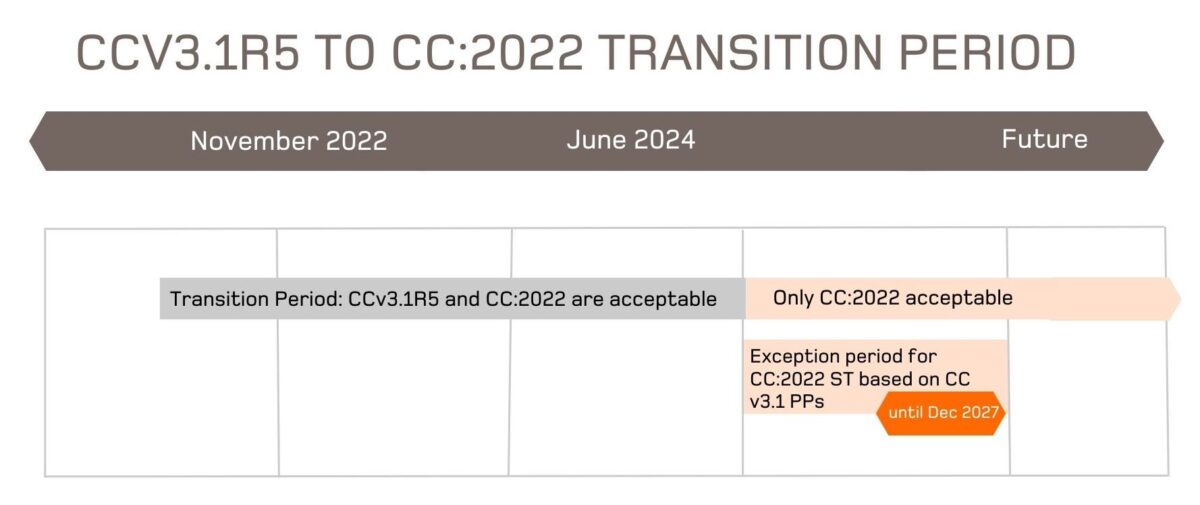
What does the new version of the CC mean for me?
Short answer: probably not much! For most vendors and users of the CC, things will roll on normally. It will be the national certification schemes, labs and technical communities that must adjust.
Long answer: there are some aspects and circumstances arising from the transition to CC:2022 that you may want to pay attention to. These are:
- Assurance Maintenance
- Using an old Protection Profile (CCv3.1) with a new Security Target (CC:2022)
- Being in the first batch of evaluations using CC:2022
We’ll dig into each of these aspects below.
Read MoreCMVP Transitions Update (July 2023)
CMVP algorithm transitions can be a great source of anxiety for vendors who seek to attain or maintain compliance to the FIPS 140-2 and 140-3 standards. A great deal of diligence, patience and persistence are required to continually review and assess product requirements against planned transitions.
Read More