NIAP recently released Labgram #118 – Entropy Source Validation Certificates. It mandates that ESV certificates must be included as part of the Entropy Assessment Report (EAR) for all products that enter evaluation with NIAP from January 1st, 2025. Effective immediately, vendors may submit EARs that refer to an ESV certificate. This blog post discusses what ESV is, how it relates to Common Criteria under NIAP and the impact of this policy on vendors undertaking evaluations outside of NIAP (e.g. Canada etc.) but seeking NIAP PCL entry.
Post-Quantum Crypto – Draft FIPS Standards Announced
In our last article on Post Quantum Crypto (PQC) titled “Introduction to the Quantum Computing Impact on Cryptography”, we introduced quantum computing concepts and the potential impact on computer security and cryptography. The article also introduced CNSA 1.0 and CNSA …
EUCC Perspectives
In this post we examine the proposed European Cybersecurity Certification Scheme (EUCC). We’ll cover:
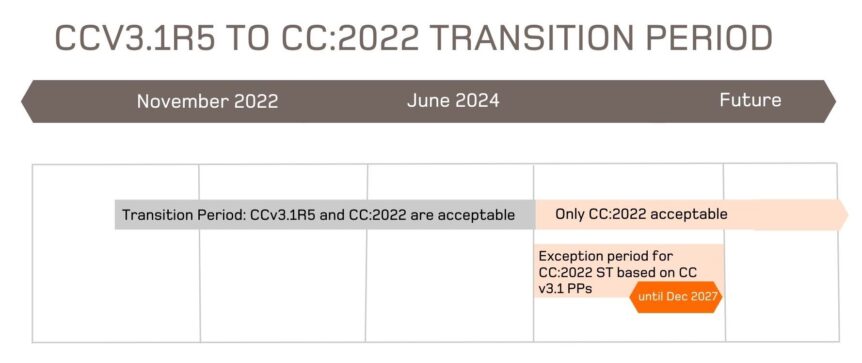
What’s the Deal With NDcPP 3.0?
NDcPP 3.0E has now been endorsed by NIAP. This post aims to answer the most common questions we get about NDcPP 3.0E:
What does the new version of the CC mean for me?
Short answer: probably not much! For most vendors and users of the CC, things will roll on normally. It will be the national certification schemes, labs and technical communities that must adjust. Long answer: there are some aspects and circumstances …
Entropy in OpenSSL 3.0
Vendors are increasingly looking to leverage OpenSSL 3.x as their cryptographic module of choice within their products. At the same time, entropy continues to a be a focus in both FIPS 140-3 and Common Criteria projects. For those transitioning from …
Introduction to the Quantum Computing Impact on Cryptography
Quantum computing continues to be a hot topic. Within the certification industry, it was most recently covered at the International Common Criteria Conference (ICCC) recently held in Spain. So, what is quantum computing and more importantly, what is the potential …
X.509 CA:FALSE Testing
Many modern Common Criteria Protection Profiles include X.509 requirements requiring the evaluator to construct a series of certificates designed to verify that a system under test is correctly parsing and validating them. X.509 certificates appear relatively simple on the surface, …
Vulnerabilities and Common Criteria
No computing system is free from security vulnerabilities. Such flaws can manifest themselves within software, firmware and hardware implementations. Often the ease in widespread mitigation is based in part on whether a vendor can provide updates to software (relatively easy), …
What’s New In App PP v1.4
The Protection Profile for Application Software (APP PP) v1.4 has recently been published. Here are some key points from our initial review. PP-Modules. Vendors are now allowed to specify additional protection profiles (PPs) and PP-Modules in a PP-Configuration with APP …