NIAP recently released Labgram #118 – Entropy Source Validation Certificates. It mandates that ESV certificates must be included as part of the Entropy Assessment Report (EAR) for all products that enter evaluation with NIAP from January 1st, 2025. Effective immediately, vendors may submit EARs that refer to an ESV certificate. This blog post discusses what ESV is, how it relates to Common Criteria under NIAP and the impact of this policy on vendors undertaking evaluations outside of NIAP (e.g. Canada etc.) but seeking NIAP PCL entry.
Read MorePost-Quantum Crypto – Draft FIPS Standards Announced
In our last article on Post Quantum Crypto (PQC) titled “Introduction to the Quantum Computing Impact on Cryptography”, we introduced quantum computing concepts and the potential impact on computer security and cryptography. The article also introduced CNSA 1.0 and CNSA 2.0 as initial suites of PQC algorithms developed by the National Security Agency (NSA). The thrust of PQC development has focused on the replacement of public key cryptography given quantum computing’s ability to conduct complex calculations quickly and potentially decrypt data encrypted with legacy algorithms in hours or days, versus the years it would have normally taken.
Read MoreEUCC Perspectives
In this post we examine the proposed European Cybersecurity Certification Scheme (EUCC). We’ll cover:
- What is EUCC?
- What is the status of EUCC?
- What has changed since the draft EUCC regulation was published?
- What impact will EUCC have on vendors?
- What impact will EUCC have on the certification industry?
- How is Lightship Security preparing for EUCC to support our clients?
What’s the Deal With NDcPP 3.0?
NDcPP 3.0E has now been endorsed by NIAP. This post aims to answer the most common questions we get about NDcPP 3.0E:
- What’s new in NDcPP 3.0E?
- What will the transition period be between NDcPP 2.2E and NDcPP 3.0E?
- What does this mean for current NDcPP projects?
- What does Lightship Security recommend for new network device projects?
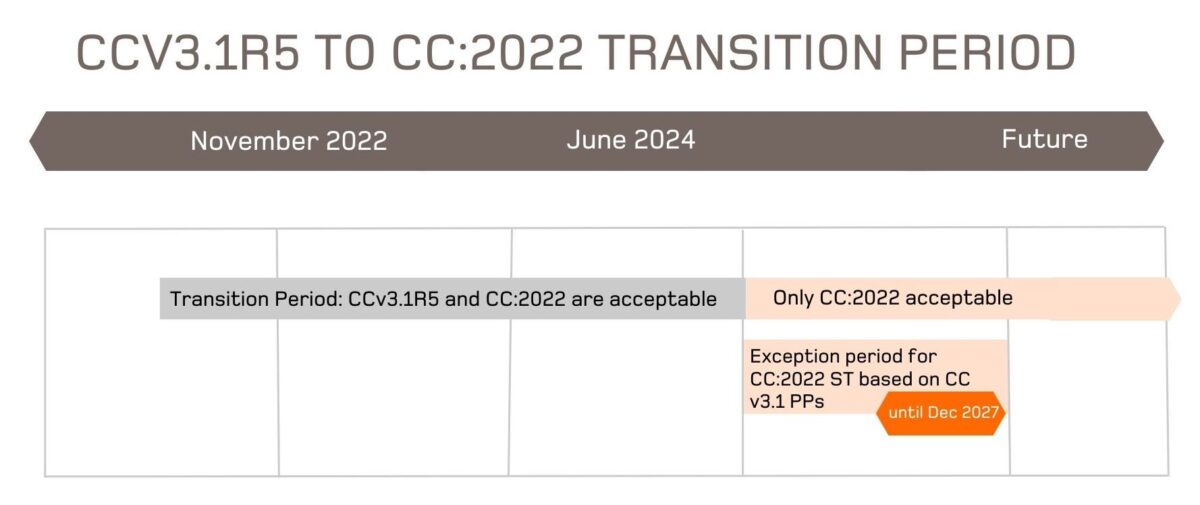
What does the new version of the CC mean for me?
Short answer: probably not much! For most vendors and users of the CC, things will roll on normally. It will be the national certification schemes, labs and technical communities that must adjust.
Long answer: there are some aspects and circumstances arising from the transition to CC:2022 that you may want to pay attention to. These are:
- Assurance Maintenance
- Using an old Protection Profile (CCv3.1) with a new Security Target (CC:2022)
- Being in the first batch of evaluations using CC:2022
We’ll dig into each of these aspects below.
Read MoreCMVP Transitions Update (July 2023)
CMVP algorithm transitions can be a great source of anxiety for vendors who seek to attain or maintain compliance to the FIPS 140-2 and 140-3 standards. A great deal of diligence, patience and persistence are required to continually review and assess product requirements against planned transitions.
Read MoreEntropy in OpenSSL 3.0
Vendors are increasingly looking to leverage OpenSSL 3.x as their cryptographic module of choice within their products. At the same time, entropy continues to a be a focus in both FIPS 140-3 and Common Criteria projects. For those transitioning from OpenSSL 1.0.2 and the FIPS Object Module 2.0.x, the ways in which entropy can seed the DRBG in OpenSSL 3.0 differs.
Read MoreIntroduction to the Quantum Computing Impact on Cryptography
Quantum computing continues to be a hot topic. Within the certification industry, it was most recently covered at the International Common Criteria Conference (ICCC) recently held in Spain. So, what is quantum computing and more importantly, what is the potential impact on computer security and cryptography? The purpose of this post is to provide a brief introduction to post-quantum cryptography – including what changes are planned to algorithm standards to proactively defend against potential security issues and when will cryptography updates come into effect? In addition, what organizations are involved in assessing requirements, proposing updates and then enforcing post-quantum solutions?
Read MoreACVP Vector Test Harness for OSSL 3.x
Lightship has released, as open source, an ACVP vector test harness for OpenSSL 3.x.
The code can be found in our GitHub repository at https://github.com/lightshipsec/ls-acvp-harness.
The README.md contains the current capabilities which we expect to update and maintain. At the moment, we include most of the typical algorithms and properties that are often claimed or required in FIPS 140-3 and Common Criteria. The full set of supported algorithms, operating modes and properties are described in the README.md. Additional algorithms can be added as needed.
Read MoreX.509 CA:FALSE Testing
Many modern Common Criteria Protection Profiles include X.509 requirements requiring the evaluator to construct a series of certificates designed to verify that a system under test is correctly parsing and validating them. X.509 certificates appear relatively simple on the surface, but digging into the details uncovers a wealth of complexity and nuance in RFC5280, ASN.1, DER, and BER. We’ll explore this testing using a specific example of the basicConstraints:CA flag and show how common X.509 tools can represent — and potentially obscure — some of the requirements as it pertains to Common Criteria conformance testing.
Read More