Algorithm validation testing is a critical path issue for FIPS 140-3 validations and for NIAP Protection Profile-based Common Criteria evaluations. Equipment vendors are often surprised at the level of effort and the potential challenges in successfully completing the algorithm testing process.
At Lightship, we have developed a suite of tools to allow us to standardize, simplify and streamline the process to obtain CAVP (Cryptographic Algorithm Validation Program) validation.
This post will outline each of the steps in addition to identifying where we will require input from the vendor.
Our CAVP certification process can be broken down into five steps:
- Algorithm Selections
- Validate Vendor and Module information
- Delivery of Demo or Production Test Vectors
- Processing Responses
- Final Submission to CAVP and CAVP Certificates Issued
The chart below shows each stage of the Lightship ACVP (Automated Cryptographic Validation Protocol) process (see Figure 1).
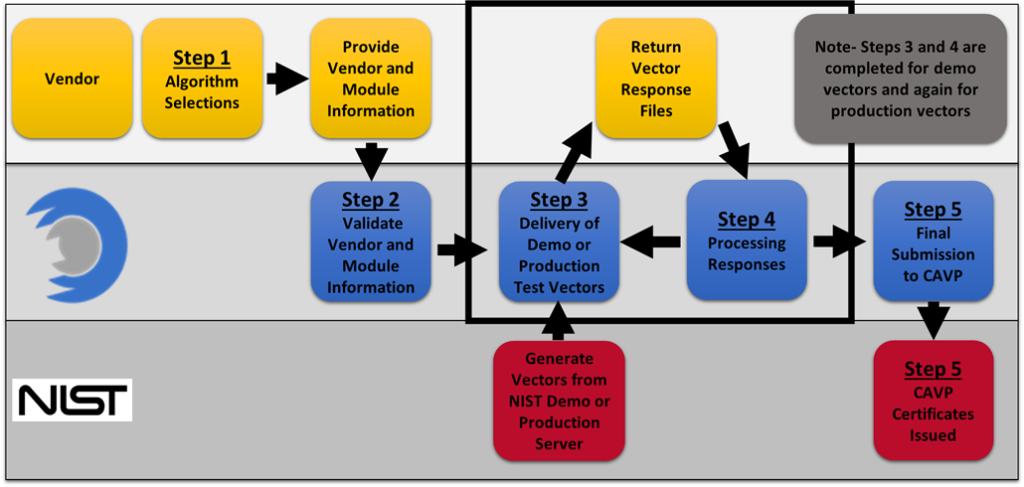
Step 1: Algorithm Selections
In order for the Lightship team to know what to provide to the vendor, details on the testable algorithms implemented in the module are required. Algorithm selections include information like key sizes, modes, and cryptographic domain parameters. For this step, Lightship and the vendor work together to determine these selections. Selections are captured using our ACVP Management Portal which gives a graphical representation of all the available options for each algorithm being tested. To ensure that the selections are correct, a vendor team member with knowledge of the cryptographic capabilities of the module being tested must be present. (If you use unmodified well-known modules such as OpenSSL, then Lightship is already aware of the low-level selections which must be made.)
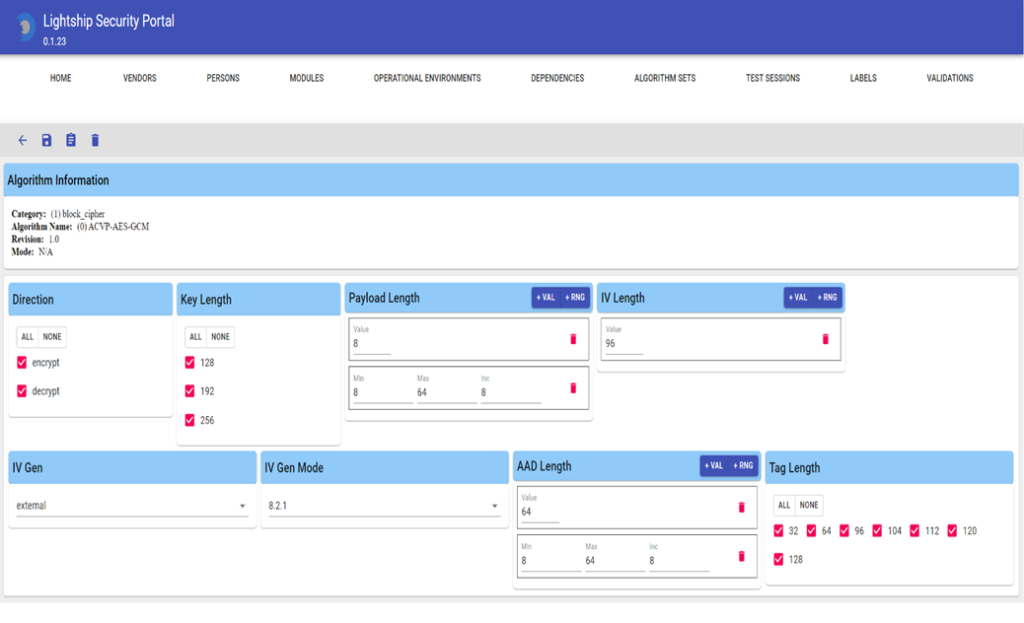
The following screenshot shows the level of detail needed to complete a selection for a single algorithm AES-GCM.
Step 2: Validate Vendor and Module Information
When creating CAVP certificates, vendor and module information must first be submitted to NIST. The module and operational environment information will be extracted from the module’s security policy if applicable, otherwise, the vendor will provide this information.
Lightship will format the information according to the ACVP specifications, send it to the vendor for review. The vendor and module information will be submitted to the CAVP as a part of the final submission process. This information will eventually be listed publicly on the CAVP certificate.
Step 3: Delivery of Demo or Production Test Vectors
After the algorithm selections are complete the customer can expect to receive a package from Lightship within the next few days containing a set of folders. These folders will contain the test vectors, known answer files (for demo vectors only), and the capability files (which are generated during algorithm selection).
Demo vectors are provided first and include the known answer files which can be used for troubleshooting. The vendor will test the vector files using their ACVP test harness. Once testing is complete, the vendor’s response files should be sent back to Lightship for validation through CAVP’s server.
Before production vectors are generated, it is required that a vendor successfully process demo vectors and ensure that their cryptographic module code is frozen. Production vector testing is the same as demo vector testing, with the exception that no known answer files are produced, and the validation process will result in formal certification.
Step 4: Processing Responses
Lightship will validate that all vendor’s demo and production responses pass. When processing responses on the demo server, the protocol allows for re-submission of failed responses. This allows customers to actively develop as testing is occurring.
When processing responses on the production server there is only one submission attempt available. If there is a failure, the vectors must be regenerated, and the testing process must be repeated until the responses are successfully validated.
NIST requires all test sessions to expire within 30 days, though this can be extended by Lightship as necessary. Once all production response files have passed, a CAVP certificate can be issued.
Step 5: Final Submission to CAVP and CAVP Certificates Issued
We made it this far and we are at the end of the certification process! With the vendor/contact/module/operational environment previously being vendor-approved, Lightship will handle all interactions with the CAVP until the validation is awarded. This process usually takes between one and two business days. When the certificate is posted on the CAVP website the link will be sent to the customer.
Cryptographic algorithm testing does not have to be difficult. Let Lightship help you navigate through the process. Contact us today!

