Updates – October, 2020
FIPS 140-3 is Here!
In this latest installment of our FIPS blog, we will cover key transition dates, available training and the list of documentation inputs needed for a FIPS 140-3 validation.
FIPS 140-3 Primer – What you need to know!
Transition Dates:
- September 22, 2020 – CMVP now accepting FIPS 140-3 submissions
- September 21, 2021 – CMVP stops accepting FIPS 140-2 submissions for new validation certificates
- September 21, 2026 – Remaining FIPS 140-2 certificates moved to the Historical list
FIPS 140-3 Project Pages: FIPS 140-3 Final and FIPS 140-3 Requirements and Management Documents
The FIPS 140-3 process from the link above is reproduced in the diagram below.
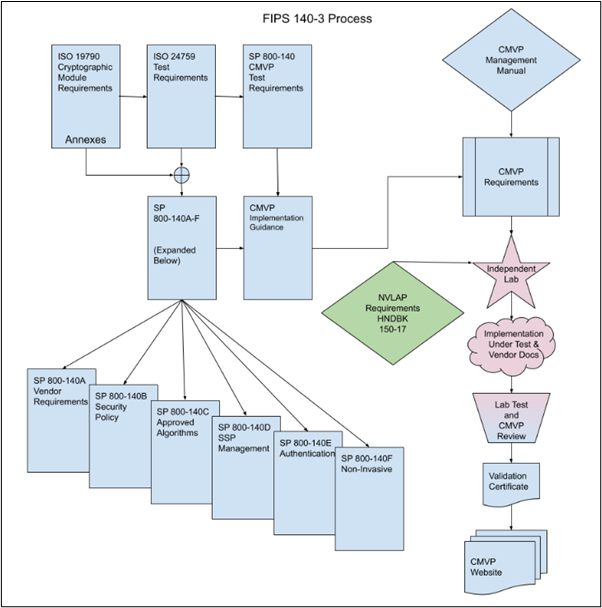
Key FIPS 140-3 Documents:
- FIPS 140-3 Standard (ISO/IEC 19790:2012: Security Requirements for Cryptographic Modules)
- FIPS 140-3 Derived Test Requirements (DTR) (ISO/IEC 24759:2017: Information technology — Security techniques — Test requirements for cryptographic modules)
- FIPS 140-3 Derived Test Requirements (DTR): CMVP Validation Authority Updates to ISO/IEC 24759 which includes links to the SP 800-140A-F documents
FIPS 140-3 online training from the Cryptographic Module User Forum (CMUF):
- The CMUF with participation from the CMVP and various FIPS testing labs have developed and presented training sessions for each of the FIPS 140-3 areas listed below:
- Cryptographic Module Specification
- Cryptographic Module Interfaces
- Roles, Services, and Authentication
- Software / Firmware Security
- Operational Environment
- Physical Security
- Non-Invasive Security
- Sensitive Security Parameter Management
- Self-Tests
- Life-Cycle Assurance
- Mitigation of Other Attacks
- CMUF training sessions:
- www.cmuf.org – Enter through the “Collaboration Tool”. (Note that you must register as a CMUF member to access the training sessions)
- Navigate to Documents > FIPS 140-3 Transition WG > Training to see a list of training presentation including text from the chat sessions.
Vendor documents required for FIPS 140-3 validation:
The following documents are typically developed by the vendor or their FIPS consultants and provided to the testing laboratory in preparation for a validation project.
See ISO/IEC 19790:2012 Annex A for a detailed list of Documentation Requirements, which includes the following:
- Security Policy (SP) – a non-proprietary (public facing) description of the module – see ISO/IEC 19790:2012 Annex B “Cryptographic module security policy” and updates in SP 800-140B.
- Vendor Evidence (VE) document – covering all assertions in the FIPS 140-3 DTR document.
- Finite State Machine Model (FSM) document – Representation of a finite state model (or equivalent) using the state transition diagram and/or state transition table that specifies all operational and error states, corresponding transitions from one state to another, input events (including data inputs and control outputs) that cause transitions from one state to another, and output events (including internal module conditions, data outputs, and status outputs) resulting from transitions from one state to another.
- Block Diagram (in SP or VE document) – depicting all of the major hardware components of a cryptographic module and component interconnections, including any microprocessors, input/output buffers, plaintext/ciphertext buffers, control buffers, key storage, working memory, and program memory.
- Bill of Materials – master components list that includes all hardware, software, and firmware components of the cryptographic module for each hardware model or GPC tested.
- Source Code Listing (SCL) – for all hardware, software, and firmware components
CMVP MIP and IUT List now showing the applicable FIPS standard:
The CMVP MIP and IUT lists have been updated to include a new column to indicate to which FIPS standard the submission applies e.g. “FIPS 140-2” or “FIPS 140-3”.
- https://csrc.nist.gov/Projects/cryptographic-module-validation-program/modules-in-process/Modules-In-Process-List
- https://csrc.nist.gov/Projects/cryptographic-module-validation-program/modules-in-process/IUT-List
Please confer with your Lightship project prime to determine how these FIPS 140-3 updates may impact your current or planned FIPS validation project.
If you need support with your FIPS validation requirements or would like to be on our FIPS updates distribution list, drop us a line at info@lightshipsec.com
FIPS 140-2/3 Updates – September, 2020
The Cryptographic Module Validation Program (CMVP) hosted a FIPS Lab Manager’s meeting on August 26, 2020. Below are the key highlights and excerpts from slides provided by NIST and Canadian Centre for Cyber Security (CCCS) that jointly make up the CMVP.
Please confer with your Lightship project prime to determine how these items may impact your current or planned FIPS validation project.
CMVP Queue – Currently about 9 months in Review Pending
- What are we (CMVP) doing about it?
- Working on adding resources -> but new reviewers take time to train
- Working on automation and changes for 140-3 that will shorten training time and reduce redundancy
- Current staffing – NIST: 10 resources and CCCS: 5 resources
- Expect reviewers to return to reports full time in September
Algorithm Process/Transitions
Key agreement – SP 800-56A Rev3 with IG D.8
- Two new scenarios, X1 and X2, were introduced, effective upon the August 2019 publication of IG D.8
- X1: Compliance with SP 800-56A Rev3: either comply with the shared secret computation (Section 6; KAS-SSC) or with the derivation of the keying material (Section 6 + Section 5.8; KAS)
- X2: The allowed schemes compliant with SP 800-56A Rev3 except that the elliptic curves are not from FIPS 186-4 / SP 800-186, but IG A.2-compliant
- On January 1, 2022, modules not compliant with either X1 or X2 will be placed on the Historical List
- Note the requirements for the CAVP testing and the KATs depending on the scenarios adopted.
Key agreement – SP 800-56Br2 with IG D.8
- Compliance with SP 800-56Br2: either comply with the shared secret computation (the Z parameter, see Sections 8.2 and 8.3; KAS-RSA-SSC) or with one of the schemes: KAS1 and KAS2 (include the key derivation; KAS-RSA)
- The transition plan:
- Vendor affirmation to SP 800-56B, if currently validated or if submitted by December 31, 2020, will remain approved through the end of 2023*
- Effective January 1, 2024, the shared secret computation in all RSA-based key agreement schemes shall be compliant with SP 800-56Br2
RSA-Based Key Transport – SP 800-56Br2 and IG D.9
- The SP 800-56Br2-compliant schemes are approved (KTS-RSA).
- Submissions with vendor-affirmed compliance to SP 800-56B may be made through the end of 2020* and, if validated, stay approved through the end of 2023.
- Submissions of all RSA-based key wrapping/unwrapping schemes with the moduli sizes of 2048+ bits may be made through 2020*. They will stay allowed through the end of 2023.
- Submissions of the PKCS#1-v1.5-compliant schemes RSA-based key wrapping/unwrapping schemes with the modulus size of 2048+ bits may me made through 2023. They will stay allowed through the end of 2023.
Key Derivation – SP 800-56C Rev2, SP 800-133 Rev2 and IG G.20
- The use of HKDF is approved (but see IG G.13 for the required justification)
- The use of the TLS 1.3 kdf is approved, see IG G.20
- SP 800-56C Rev2 shows randomness extraction followed by multiple key expansions
- SP 800-133 Rev2 section 6.3 includes a new key derivation scheme
Entropy – SP 800-90B, IGs 7.18 and 7.19
- November 7, 2020*. After this date, all new submissions shall be SP 800-90B compliant.
- IG 7.19 should help vendors and labs comply with the requirements of SP – 800-90B. Note: IG 7.19 has now been published in the latest IG document (August 28, 2020).
- The difficult task that every validation faces is producing a heuristic proof that the claimed amount of entropy has been generated
- (Labs) Submit an entropy source design to the CMVP for a pre-review
- SP 800-90B compliance is required for FIPS 140-3
Vendor Affirmation Transition – September 1st, 2020
- AES-CBC-CS (Addendum to NIST SP 800-38A) – IG A.12
- PBKDF (NIST SP 800-132) – IG D.6 (Note: vendor affirmation now allowed until 31 December 2020 for FIPS 140-2)
- AES FF1 (NIST SP 800-38G) – IG A.10
- cSHAKE, TupleHash, ParallelHash, KMAC (NIST SP 800-185) – IG A.15
- RSA 4096-bit modulus (FIPS 186-4, NIST SP 800-131A Rev. 2) – IG G.18
- ANS X9.42-2001 KDF (NIST SP 800-135 Rev. 1)
- Higher level algorithms using FIPS 202 functions – IG A.11.
Vendor Affirmation Transition – December 31st, 2020
- KAS IFC (NIST SP 800-56B Rev. 2) – IG D.8
- KTS IFC (NIST SP 800-56B Rev. 2) – IG D.9
- KAS-SSC FFC/ECC (NIST SP 800-56A Rev. 3) – IG D.1-rev3
- Key-Derivation Methods in Key-Establishment Schemes (NIST SP 800-56C Rev. 2) – IG D.10
- Note: Testing for functions (KAS IFC, KTS IFC, KAS-SSC FFC/ECC) will be available by 30 September 2020.
Vendor Affirmation Transition – Going Forward
- CAVP algorithm or algorithm component testing released during these dates would be followed by CMVP Transition dates:
- 01 July to 30 Sept 2020: 31 Dec 2020
- 01 Oct to 31 Dec 2020: 31 March 2021
- 01 Jan to 31 March 2021: 30 June 2021
- 01 April to 30 June 2021: 30 Sept 2021
Example: if the CAVP releases new testing for algorithm A, B and C, during the 01 July to 30 September period, then the transition date will be 30 September + three months, so 31 December, where after that date vendor affirming to algorithms A, B, or C will be prohibited in submitted reports.
Other transitions are forthcoming
- The Triple-DES – SP 800-67 Rev2, IG A.13
- From FIPS 186-4 to FIPS 186-5 and the SP 800-186 elliptic curves
- SP 800-90C
FIPS 140-3 Implementation Guidance
- 140-3 IG comments are being reviewed and FIPS 140-3 is scheduled to be published before September 22, 2020 (when FIPS 140-3 reports can be submitted to CMVP).
New FIPS 140-3 1MU submission type will be introduced
- 1MU submission type will be introduced as a “maintenance” update in place of 1Sub for FIPS 140-3. Instead of arguing as to the security relevance, we will be introducing Scenario 1MU – Maintenance Update, which can be submitted for up to 1 year post validation for changes up to 30%, but will not have a new certificate and sunset dates will not be updated. There will be no cost recovery fee for a 1MU.
If you need support with your FIPS validation requirements or would like to be on our FIPS updates distribution list, drop us a line at info@lightshipsec.com
FIPS 140-2/3 Updates – June 23, 2020
2020 continues to bring several significant changes to the FIPS 140 program landscape. Evolving algorithm and program transitions happening this year make it hard for vendors to stay up to date on all of the various activities and deadlines. To help, we provide our FIPS clients with regular updates on programmatic status and highlight possible areas that will impact existing or pending validation efforts.
Breaking FIPS 140-2 Update: On June 23rd, the CMVP announced the following important transition reminders and updates to a few key algorithms such as NIST SP 800-56A Rev. 3
Please confer with the testing experts at Lightship Security to determine how this announcement impacts any current or planned FIPS 140-2 validation project.
From the CMVP:
The following is a list of upcoming algorithm transitions, along with their dates and actions that will be taken because of the transition.
FIPS 186-2 -> FIPS 186-4 (Per IG G.18)
- Transition date of September 1, 2020. On September 1, 2020 all modules tested to FIPS 186-2 for any RSA-based functionality other than signature verification (with any modulus length) and signature generation with nlen=4096 will be moved to the historical list. Please see IG G.18 for more details.
(Note: Modules that support testing to FIPS 186-2 RSA SigGen only at 4096-bit modulus size will not be moved to the historical list because FIPS 186-4 SigGen testing at 4096-bit modulus was not made available until ACVP was later developed and 4096-bit testing was only available in FIPS 186-2 form via CAVS.)
SP 800-90B (per IG 7.18)
- Transition date of November 7, 2020. After November 7, 2020 the new submissions and the revalidations extending the lifetime of the module shall demonstrate compliance to SP 800-90B (if entropy estimation is applicable per IG 7.14).
- NDRNGs will be grandfathered, i.e. they will be allowed to be used in Approved Mode. Modules using them will remain on the active list.
IG D.8 (SP 800-56Arev3 and SP 800-56Brev2) – Key Agreement
- January 1, 2021 – The CMVP will not accept modules submissions with non-56Arev3 and non-56Brev2 compliant implementations in Approved Mode.
- January 1, 2022 – The CMVP will move all modules with non-56Arev3-compliant implementations in Approved mode to the historical list.
- January 1, 2024 – The CMVP will move all modules with non-56Brev2-compliant implementations in Approved mode to the historical list.
- The CMVP will allow modules with non-56Arev3-compliant implementations in Approved Mode to get validated after January 1, 2021, as long as the module submission was before January 1, 2021.
- The CMVP will allow modules with non-56Brev2-compliant implementations in Approved Mode to get validated after January 1, 2021, as long as the module submission was before January 1, 2021.
IG D.9 (SP 800-56Brev2) – Key Transport
- January 1, 2021 – The CMVP will not accept modules submissions with non-56Brev2 compliant implementations, with the only exception being if the scheme only uses a PKCS#1-v1.5 padding scheme as shown in Section 8.1 of RFC 2313.
- The CMVP will allow modules with non-56Br2 compliant implementations and non-PKCS#1-v1.5 schemes to get validated after January 1, 2021, as long as the module submission was before January 1, 2021.
- January 1, 2024 – The CMVP will move all modules with non-56Brev2 compliant implementations in Approved Mode to the historical list.
Triple-DES (SP 800-67 Rev2)
- January 1, 2024 – The CMVP will move all modules that support Triple-DES Encryption in the Approved Mode to the historical list.
- The Triple-DES decryption, including its use in key unwrapping, will continue to be approved (for legacy use only) after December 31, 2023.
If you need any support with your FIPS validation requirements or would like to be on our FIPS newsletter distribution list, drop us a line at info@lightshipsec.com
FIPS 140-2/3 Updates – June 9, 2020
2020 is bringing several significant changes to the FIPS 140 program landscape. After years of being relatively static, this year marks the transition to the long-awaited new version of the standard – FIPS 140-3. Also new for this year is the rollout of the Automated Cryptographic Validation Testing System (ACVTS) starting in July. This marks a significant change in the process for how vendors need to validate their cryptographic algorithms going forward.
These changes, plus the numerous algorithm transitions happening this year make it hard for vendors to stay up to date on all of the various activities and deadlines. To help, we provide our FIPS clients with regular updates on programmatic status and highlight possible areas that will impact existing or pending validation efforts.
FIPS-related updates and reminders for June 11, 2020:
- The CMVP are now granting an extension of permission to do remote testing until August 31, 2020. They will continue to monitor the situation and update this guidance as needed. For vendors, this means that functional testing may be completed remotely by the lab to avoid travel during COVID19.
- The Cryptographic Module Users Forum (CMUF) have a new website (https://www.cmuf.org) which is now up and running. Check it out!
- NIST Special Publication (SP) 800-133 Rev. 2, Recommendation for Cryptographic Key Generation – now available here: https://csrc.nist.gov/publications/detail/sp/800-133/rev-2/final – See “Appendix A: Revisions” for details.
- Cryptographic Algorithm Validation Program (CAVP) retirement and transition to ACVTS :
- CAVS (legacy algorithm test tool) based submissions end as of June 30th, 2020. Contact Lightship to get assistance with your ACVP transition e.g. sample JSON formatted vector sets.
- Please refer to the CAVP website for details on new testing supported by ACVP: https://csrc.nist.gov/Projects/cryptographic-algorithm-validation-program/cst-lab-transition
- Further information : https://lightshipsec.com/comparing-cavp-and-acvp-test-harness-implications/
If you need any support with your FIPS validation requirements or would like to be on our FIPS newsletter distribution list, drop us a line at info@lightshipsec.com
James Ramage
James Ramage is a senior FIPS evaluator at Lightship. He has been doing FIPS evaluations and security certifications for 5+ years and enjoys working with customers, training team members and evaluating new technologies.

